Biden’s Cyber Conundrum: Virtual Invasion – Analysis
By Observer Research Foundation
By Vivek Mishra and Sachin Tiwari
Introduction
Chinese cyber activities have been described as the most active, broad, and persistent threat, as per the Annual Threat Assessment of the US Intelligence Community brought out last month. The report concludes that at the heart of a decade-long campaign of making China a cyber power lies the fusion of military and civilian organisations.
With the rise of China and its global impact, hacking operations have been conducted globally targeting telecom, defence, intellectual property, and classified information. According to the Microsoft Defense Report 2022, the major share of the top targeted country remains the United States (US) at 54 percent. However, the cyber activities have included other countries from Africa, West Asia, Southeast Asia, and the island nations in the Pacific and the Caribbean.
The extent of these cyber-attacks is expansive and is targeting neighbouring ASEAN states to steal sensitive data. The ransomware attack on one of the largest public health institutions in India, AIIMS and its link to China-sponsored hackers is the continuation of the cyber-attacks which targeted the electric grid in India in 2022 after the border clashes as well as another at the strategic location of Ladakh. These attacks have not just affected physical security but have proven anticipatory of a dangerous precedent across the Indo-Pacific due to the cyber threats from China in the region.
Wave of stealthy attacks
The US has been witnessing a wave of stealthy cyber-attacks and espionage from China. According to the latest findings by Google Mandiant, there is a change in the sophistication of attacks from the earlier espionage attacks conducted by China, especially focusing on zero-day exploits, vulnerabilities that are still not known.
There have been reports of directly targeting the supporting system such as firewalls and other network systems such as VMware that form the backbone of operations. There have been targeting of systems that are difficult to penetrate such as routers allowing them to control the timing of the attack and making the connection to the system.
An exploit affecting Fortinet, a US-based cybersecurity company was targeted by a zero-day exploit that allowed the capability to write and execute malware targeting large organisations. The attackers have a sophisticated knowledge of the system and were able to reverse engineer the system. These are the backbone network devices that are used by the major government and private companies in the US as well as outside and access to them allows access to several exploits.
These attacks are in continuation of major cyber-attacks such as the Microsoft exchange emails that compromised over 30,000 companies in the US and targeted several thousand organisations worldwide, leading to the wide condemnation by the Biden administration along with allies.
Already, ransomware attacks have proven to be a challenge with their rising number during the COVID-19 pandemic and major incidents like targeting of the major supply chain such as the Colonial pipeline, and the SolarWinds hack had a massive public impact. The issue of industrial-level espionage is proving to be a high ranking threat in the US with the theft of intellectual property and defense secrets by Chinese actors. If anything, instances of balloon spying have further added to these concerns.
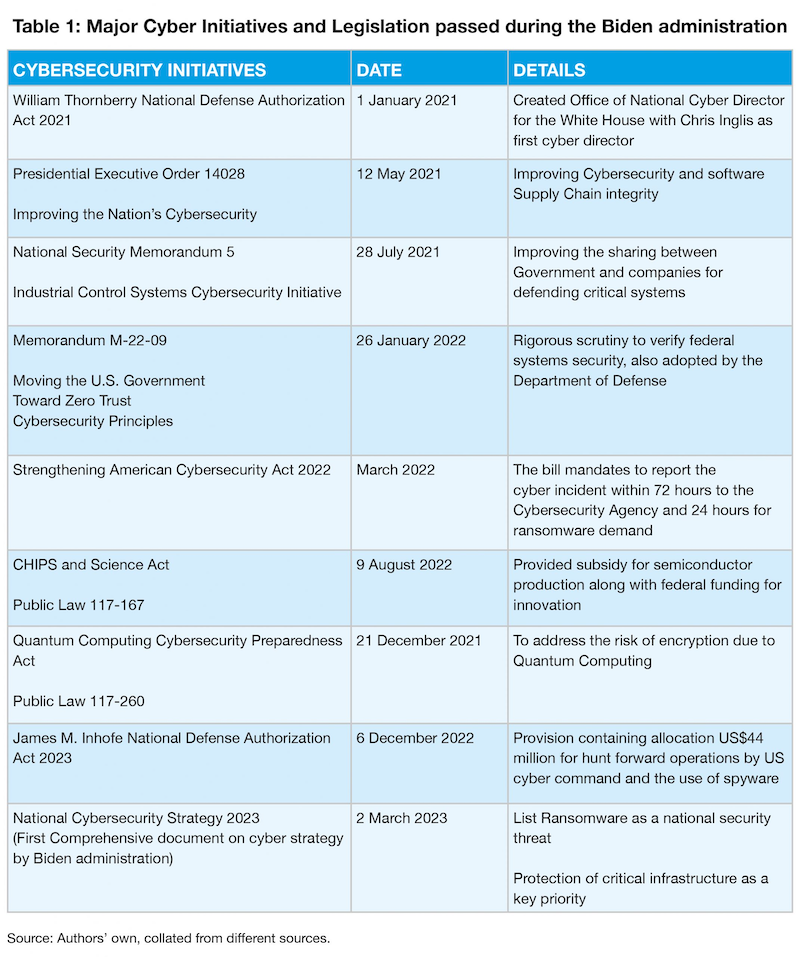
Biden’s preparedness
Amidst some major threats, disruptions and supply chain vulnerabilities caused by large scale cyber-attacks in the US, the Biden administration has taken a few steps. In October 2022, the Biden administration launched the International Ransomware Initiative to counter the issue of criminal actors in the global cyber space.
Another step has been with regard to managing the private sector that has been operating on a voluntary basis leading to delays in reporting and sharing of information on cyber-attacks and espionage. The Biden administration pushed for legislation on critical infrastructure reporting by the entities.
However, entities and stakeholders are still debating on the compulsory obligation clause imposed on the software vendors for reporting cyber-attacks within 72 hours and ransomware attacks within 24 hours to the Cybersecurity and Infrastructure Security Agency (CISA) of the U.S. Department of Homeland Security.
Other efforts by the Biden administration include efforts to integrate such practices with its global partners, in particular the endorsement US led-Counter Ransomware Initiative by the Quad members—India, the US, Australia and Japan—to facilitate sharing of information and take collective action.
Apart from the managing cyber threats to the private sector, the Trump administration had led discussions on policies to target the source of cyber-attacks. The aggressive policy has led to the taking out of the troll farms in Russia that targeted US elections both in 2016 and 2020. The Biden administration in 2022 announced US$10 million for more information on Internet Research Agency, a Russian troll farm. The policy has been endorsed in the form of integrated deterrence under the Biden administration i.e. the use of all means to deter the attacks.
A more aggressive approach is being released with the use of intelligence and military operations for the disruption of cyber activities outlined in the recently released National cybersecurity strategy 2023.The cyber conundrum for the US is not new and had escalated with China during the Obama administration in 2015, leading to the formation of the 2015 cyber agreementon the conduct of industrial espionage.
However, the conditions were set aside with a report of increasing Chinese cyber activities as specified in the IP commission reportand other House reports. It came at a time of demand for a more proactive policy against China leading the Trump administration to recognise China among the principal competitors involved in widespread espionage and the threat to American innovation and the wider tech sector.
Several Executive Orders and bills were passed in Congress. These include the Foreign Investment Risk Review Modernization Act 2018 and actions by the Bureau of Standards that controls the investment from foreign companies in the strategic sector, especially telecommunications such as Huawei and ZTE under export regulation.
The debates in the US Congress have further intensified with the formation of the US Cyberspace Solarium Commission for identifying threats in the cyber domain. An important recommendation from the commission was boosting investments in the sector to create effective deterrence as well as strengthen American industry.
These policies have been followed up by the Biden administration with the singling out of China as the principal concern as outlined in the NSS 2022. The bipartisan Chips and Science Act that provides incentives to domestic manufacturing promises long-term investments in science development to maintain innovation, bearing similarity to the US efforts to boost Sematech in the 1980s.
At the global level, the US identifies a host of countries as existing and potential threats in the cyber domain. China along with Russia and Iran have been recognised as major cyber adversaries which have been actively operating against US interests.
The declaration by Russia of its partnership as a friendship with no limits with China is particularly alarming for a potentially strengthening cyber axis against the US. Similarly, Iran’s supply of the Shahed drones to Russia points to other possibilities in tech cooperation between Russia and Iran. China itself has been closely working with Iran. One of the successes of that partnership is the brokering of the peace dealbetween Iran and Saudi Arabia, two long-standing adversaries.
In the cyber domain, with Iran’s comparatively less lethal technologies and capabilities with only a few instances of cyber-attacks on the US and Israel in the past points, the possibility of collaboration of groups and stakeholders from China or Russia supported by the other states cannot be ruled out. The assessment of threats in the cyber domain is very high with thousands being arrested last year in an Interpol crackdown.
For the US, the threats in the cyber domain to its elections is an obvious one, given past trends. The Russian disinformation campaign in 2016, the repeated attempts in the 2018 midterm elections to sabotage the processes and the Chinese threats to the 2022 midterm elections have posed significant risks in anticipation of the upcoming national elections in 2024 and further anticipation in the upcoming elections.
As the US, India, and the European Union (EU) all go into elections in 2024, the need for an effective international bulwark against cyber-attacks cannot be overstated.